Thursday, July 31, 2008
In China, Censorship is Called Security
This shouldn't surprise anyone. Although they consistently deny it, China has a history of spying on both business and government visitors. They also consistently get accused by governments around the world of hacking into sensitive systems.
Recently, there was a lot of speculation that Commerce Secretary Carlos Gutierrez's laptop was hacked during a visit to China and the information was used to hack into government computers. Saavy business types have been quoted as saying that they do not carry laptops or smartphones with them while travelling in China. Of course -- if you needed some more substantial proof China is behind a lot of espionage -- you could read about all the people getting caught by the FBI stealing sensitive information for the People's Republic.
Senator Brownback made a statement on Tuesday that he was warned that the Chinese Public Security Bureau has made it mandatory for hotels chains to install spyware and special hardware by the end of July. Failure to install the required items (or disabling them afterwards) will lead to "punishment," according to a document in the Senator's possession.
Of course, all this is being done in the name of security, according to People's Republic officials. Oddly enough -- possibly to address privacy concerns -- they plan to employ pop up windows warning people the Internet is not private in China. I'm sure this is assuring to privacy advocates, worldwide (pun intended).
The Senator's staff handed out English language translations of two separate documents he said were received by hotels, outlining the government's instructions on how to implement Internet spying software and hardware by the end of July to members of the press on Tuesday.
In many people's opinion -- the intention of this security system is monitor people -- who might want to expose China's dismal human rights record during the games. In fact, Senator Brownback was initially warned about these so-called security measures by human rights advocates.
Further evidence of this is that on Tuesday access to sites like Amnesty International or any with a Tibet address were being blocked at the main Olympic press center in Bejing, according to the article in the Los Angeles Times on this story.
Senator Brownback announced during the conference that he and Senator Bunning of Kentucky were introducing a resolution calling on China to suspends it's plan to censor free speech and spy on people. It should be noted that years ago -- when bidding for the games -- China promised to not to do this.
While many speculate the intent of this so-called "security system" is to supress free speech (censor people), I'd highly recommend anyone with sensitive information be extremely careful if they are in China during the Olympic games. The real espionage and hacking will not be as apparent as this has been. A good place to learn about Chinese hacking and espionage is the Dark Visitor site, which should give anyone a good idea what information risks they might face during a visit to China.
Sunday, July 27, 2008
Fraud, Greed and Special Interests in the Mortgage Crisis Cost Everybody

(Actual photo of an an allegedly remodeled condo courtesy of the FBI)
If you think the factors that enabled the mortgage crisis have been fixed, think again.
An example of this might be the Tennessee minister (Reverend Steve Young)-- awaiting sentencing after pleading guilty to mail and wire fraud to commit mortgage fraud -- who was recently rearrested to protect the general public. While out on bond, Reverend Young was using the identities of members of his parish to obtain more fraudulent mortgages, according to an article I came across in commercialappeal.com.
Apparently, members of his parish turned Reverend Young in after discovering the mortgages when reviewing their credit reports. Of course, it is considered wise to review your credit report on a regular basis after already being exposed to identity theft.
With the current mortgage crisis going on the story of Reverend Young is just one of many examples of fraud, greed and corporate bailouts in the mortgage crisis. In April, the FBI released the 2007 Mortgage Fraud Report. The report refers to this type of fraud as a low risk, high yield enterprise. Maybe we wouldn't see so much mortgage fraud if it weren't so low risk and extremely profitable?
According to the report, the victims of mortgage fraud are many. They include the people living in the neighborhoods where the fraud occurred, borrowers, and the mortgage industry, itself. For instance, when properties are sold at artificially inflated prices, property taxes increase. After the bubble bursts and the fraud becomes apparent, sellers have a difficult time selling their homes because they owe more than what the house is worth. This leads to foreclosures and can cause neighborhoods to deteriorate, which tends to lower all the property values in the area.
With the release of the 2007 report, the FBI announced Operation Malicious Mortgage, which to date has netted an impressive amount of arrests. The latest in this ongoing operation are rumors that the FBI is investigating a major lender, IndyMac for mortgage fraud. Despite the arrests, a lot of people are still suffering after getting caught in up one of the schemes that contributed to where we are at today.
One of the better publications covering mortgage fraud is the Mortgage Fraud Blog. It has up-to-date information on Operation Malicious Mortgage and on the subject in general.
One might think now that we are well on our way into the mortgage crisis, fraud related to mortgages would be going down. Sadly, this isn't the case and the story of a minister released on bond after being convicted for mortgage fraud -- then rearrested for the same thing bears out this contention.
Another, even sadder twist are the desperate homeowners being taken in by scammers promising to rescue them from their current situation. Besides greed, fear is a often used method to snare victims in fraudulent schemes. In May, the Comptroller of the Currency Administrator of National Banks (Treasury Department) issued a warning on this subject. Some of the scams include what are known as lease-back or repurchase scams, refinance fraud and bankruptcy schemes. Quite often, these schemes are nothing more than a means to steal whatever equity the person being foreclosed on has in the property, leaving them with nothing.
Bringing the mortgage crisis down to a more human level is the HousingPANIC blog. The blog is a wealth of information from the consumer point of view and keeps track of high-profile types recently arrested for mortgage fraud.
Thus far, in what has been termed the mortgage crisis, we've seen the banking industry get bailed out (at taxpayer's expense), a lot of people getting arrested, but so far very little help for the people getting foreclosed.
I've seen this being rationalized as it's their own fault because they knew they were getting in over their heads. While this is true -- especially in the case of the big players in the mess -- many of the smaller players were being wooed, coerced and simply taken advantage of. To me at least, this bears consideration.
Finally, it appears that some help for the little people losing their shirts is on the way and the Senate finally got it together and passed a bill. The bill is expected to be signed by President Bush with "reservations." In reality this bill (H.R. 3221) extends a lifeline to Freddie Mac and Fannie Mae by allowing people being foreclosed on to convert to government loans. Freddie Mac and Fannie Mae have about $5 trillion in mortgages, which accounts for about half the outstanding loans in the United States.
Interestingly enough, it is being reported by the AP, that Senator Jim DeMint, R-South Carolina was banned by the Democratic leadership from calling for a vote to stop the companies benefiting from this from making political donations or lobbying for this bill. Apparently, although facing bankruptcy, these companies have enough money to spend on lobbyists and political contributions? In fact, Freddie Mac and Fannie Mae spent about $3.5 million in the first quarter of this year on lobbyists.
While I'm glad about half of the little people are finally getting some help, I have to question at what cost? The sad truth is that we (taxpayers) will pay for this and as usual, special interests and not the interests of the public seem to have too much influence in the decision process.
Another question yet to be answered is what happened to all the money these large corporations made during the housing boom? It appears the profits I'm referring to are made private, while the costs incurred from deceptive business dealings become public? To me, this is another example of how special interests can spin political outcomes in their own favor.
Of course, the even sadder truth is that the economy can't suffer too many more large employers posting large losses or going under. When this happens a lot of the little people working for them become unemployment statistics. This is probably the sad reality of the situation. There is little doubt, we need to fix the problem, but are we going about it in the most just manner?
I've often wondered how much better off we would all be if special interests (lobbyists) were banned, altogether? Given all the polls -- clearly showing a lack of confidence in our leaders -- watching special interests consistently receive preferential treatment is probably one of the reasons why. Perhaps, we would have more confidence in them, if we felt they were representing us in consideration for all the taxes we are being asked to pay.
Saturday, July 26, 2008
DNS Cache Poisoning Opens Doors for Internet Criminals
DNS Cache Poisoning is a flaw in what is referred to as the domain name system (DNS) that allows domain names like "Walmart.com" to be changed into numeric code. In layman's terms, this makes it easier for networking hardware to route search requests. When exploited by hackers, the flaw could allow them to redirect Internet users to malicious sites.
Security Resercher, Dan Kaminsky -- who discovered the flaw several months ago -- reported it to the authorities and had been working in secret with the major security vendors on a fix. The plan was to coordinate a response before criminals discovered the flaw and started exploiting it. In March, experts from all over the world met at the Microsoft campus to put this plan into motion. On July 8th, patches were shipped from the major security vendors to protect systems against the flaw.
They were hoping this would give everyone 30 days to patch their systems, but it didn't work out the way it was supposed to.
On Wednesday, instructions how to use this flaw were posted on the Internet. Subsequently, these "instructions" (computer code) were put into a hacker tool called Metasploit, which makes them easy to use by not very technically inclined criminals.
Easy to use tools, sometimes referred to as DIY (do-it-yourself) kits, have been blamed for the ever increasing crime levels we see on the Internet today. They are sold fairly openly and sometimes even come with technical support.
Metasploit is open source computer project used to research exploits and vulnerabilities. While considered a useful tool by researchers, it can also be used by criminals to exploit vulnerabilities within systems.
Dan Kaminsky did an interesting blog post explaining this in detail that contains a DNS Checker to see if your internet service provider (ISP) has patched the flaw. I highly recommend everyone tests their system using this tool!
Thanks to this information being released on the Internet before everyone could get their systems fixed, the first attacks using this flaw are being seen in the wild (on the Internet). Yesterday, James Kosin announced on his blog that the attacks are starting and it's time to patch or upgrade now. Websense also announced the same thing with a security alert.
Impromptu research by Kaminsky reveals that as of yesterday just over 50 percent of the unique name servers are vulnerable to this attack. On July 9th, roughly 85 percent of the unique name servers were vulnerable. Undoubtedly, there are a lot of computer security types working this weekend.
Individual users, who have their systems set for automatic updates probably will receive the patch as soon as it's released by their provider. Please note that older systems might still be vulnerable until they are updated.
Robert Vamosi at CNet has aptly pointed out that home users might need to patch, also. Handy links to do so are linked from the article, he wrote on this.
I guess the best thing for us "little people" to do is to make sure our systems are updated. I would recommend doing it manually if you aren't set up for automatic updates.
Further details of this will be covered by Kaminsky at the upcoming Black Hat Conference scheduled on August 6th.
Wednesday, July 23, 2008
Will One Spam King's Conviction and Another's Escape Mean Less E-Trash on the Internet?
For his misdeeds, Soloway was sentenced to just under four years. Notably, Soloway was the second person to be prosecuted under the Can-Spam Act. It should also be noted that the prosecutors asked for about twice the time in prison and with good behavior, Soloway will probably only serve about half of the sentence he received.
Like most of the many "Spam Kings" out there, Soloway allegedly used a botnet (army of zombie computers) to saturate the electronic universe with e-trash, including advertisements from commercial clients. To give everybody an idea of the scope of Soloway's activity, he allegedly sent out 90 million e-mails in a three-month period.
The made me wonder if anyone is looking at the commercial clients? Of course, everyone knows that "Spam Kings" send out a lot more than commercial advertisements, including a variety of scams designed to steal from unwary people. They also tout knock-off drugs, merchandise, software and porn.
Spam is also used to deliver malicious software, which can steal all your personal and financial information. Ironically, spam also delivers malware designed to turn a system (part of a botnet), which is then used to send out even more spam.
In fact, spam designed to send out even more spam best describes Soloway's operation. Using a company, Newport Internet Marketing Corporation (NIM), he offered a broadcast e-mail software product and broadcast e-mail services. His website promised a full refund if a customer wasn't satisfied, however in reality, if anyone ever complained they were threatened with financial charges and collection agencies.
According to the Department of Justice press release, one customer tried to complain about the amount of spam he was getting and Soloway's response was to send him even more spam.
The press release also mentions that he willfully failed to pay his taxes after earning more than $300,000 in 2005.
Interestingly, enough another "Spam King," Edward "Eddie" Davidson simply walked out of a minimum security facility in Colorado about the same time Soloway was sentenced. Davis allegedly made $3.5 million spamming for about 20 commercial clients. Like Soloway, he failed to pay any taxes on the proceeds of his misdeeds.
Unfortunately, Soloway's conviction or Davidson's escape is unlikely to make much of a dent in spam anytime in the near future. Earlier this month, Symantec reported blocking 3.5 million spam messages over the 4th of July holiday. Their monthly spam report reported that over 80 percent of all e-mail sent is spam. The 80 percent statistic (and greater) has been a sad fact for several months now.
Notable trends on the last report included using the China earthquake to spread viruses and the use of fake new flashes (like U.S.A. attacks Iran) to net Internet crime victims.
We probably shouldn't be too quick to celebrate Soloway's conviction. He is obviously just one of many "Spam Kings" operating out there. Hopefully, as time goes on, we will see more of these so-called spam superstars put behind bars. After all, just about anything that is distasteful or illegal on the Internet normally starts with a spam e-mail.
On a final note, both Soloway and Davidson seemed to be servicing a lot of commercial clients. Maybe if the legal emphasis shifted towards the people paying spammers, there would be less incentive (money) for spammers to pollute the Internet!
Update (7/25/08): In a horrifying twist to Eddie Davidson's escape, it has now been reported by the AFP that he killed himself after killing his wife and their three month old daughter. Davidson's seven month old son was left in the car unharmed and his sixteen year old daughter was shot in the neck before escaping.
Given these circumstances, I wonder if anyone is going to question why Davidson was locked up in a minumum security facility that he was able to walk away from?
Monday, July 21, 2008
E-Gold Admits Being Guilty of Enabling Internet Criminal Activity
The three executives in question, Dr. Douglas Jackson, principal director of E-Gold and CEO of Gold & Silver Reserve Incorporated, and two of his senior directors (Barry Downey and Reid Jackson) pleaded guilty to conspiring to engage in money laundering and operating an unlicensed money transmitting business.
The corporations involved (E-Gold and Silver Reserve) face a fine of $3.7 million and have already agreed to pay a judgment of $1.75 million. Jackson faces up to 20 years in prison and a fine of $500,000 and Downey and Reid face a maximum of 5 years in prison and a $25,000 fine.
Anonymous means of transmitting money are favorite ways for criminals to conduct illegal business and scam people. In the current case, the Department of Justice charged that the criminal activity included investment scams, credit card fraud, identity theft and even child exploitation.
They did mention that E-Gold assigned employees to monitor accounts for fraud, but the employees allegedly didn't have any previous experience in dealing with illegal activity.
Another article in PC World about this story pointed to a blog post, where Douglas Jackson announced some new security procedures to verify their customers and prevent fraud. No new accounts are being opened until they can find out an "interim means" of verifying who their customers actually are. Also mentioned in the blog post was that a systems design flaw made it difficult for them to get rid of a user, effectively. The logic behind this seems to be that if one account was blocked another one would be opened. Please note that with all kinds of free e-mail accounts -- which was the only requirement to open an E-Gold account -- it wouldn't be very hard for a criminal to simply move on to another e-mail address if they got caught committing fraud.
It will be interesting to see how they plan to verify customers over the Internet.
In 2006, BusinessWorld reported that the ShadowCrew -- a 4,000 strong credit card fraud and identity theft ring operating in carder forums on the Internet -- used E-Gold to launder some of their proceeds.
To anyone familiar with crime on the Internet, allegations of criminals using, or manipulating E-Gold (or other services like these) are nothing new. E-Gold gives their customers the ability to transfer the value of gold, electronically. To transfer E-Gold -- which has a cash value -- all anyone needs is an e-mail address, account number and password.
E-Gold type accounts are also prone to take-overs. This normally occurs when account numbers and passwords are stolen via what is known as phishing and the account is taken over by a fraudster. After a crook compromises the account in this manner, they simply transfer the gold, elsewhere. Phishing is accomplished using social engineering or sometimes with the help of malware (crimeware) that automatically steals all the information from a system using keylogging software.
Please note from what I've heard, people are never made whole (compensated) after this happens to them. Once the money is transferred, there is little or no recourse to be had by the account owner. Interestingly enough, E-Gold spins this as there are no chargebacks to worry about. Chargebacks occur when a financial institution discovers a financial instrument was used to commit fraud and the transaction is charged back to the merchant.
So far as the money laundering aspect, a anonymous service such as E-Gold can be used to move the proceeds of all sorts of crimes. People are known to be duped in job scams to launder money using a service like this. In cases like these, they are taking all the risks for a small portion of the rewards.
In most instances, anyone who gets involved in one of these scam activities is going to at the very least lose their shirt in the process. Of course, they can also get arrested.
The best thing to do is to be extremely careful when someone offers you riches, or "gold" over the Internet. There is a difference big between real gold and what is known as "fools gold."
Sunday, July 20, 2008
Rapper DMX Charged With Medical Identity Theft
Apparently, DMX used the name Troy Jones when seeking medical care for pneumonia, according to KNXV-TV in Phoenix. He also used a social security number that didn't belong to him. Allegedly, DMX did this to get out of paying a $7500 bill.
Earlier this month, DMX was arrested at Sky Harbor Airport in Phoenix for outstanding warrants. He was flying into Phoenix after being arrested for drugs in Florida. Maybe the reason, he doesn't have the money to pay his medical bills is because of all the drugs he buys (speculation)?
Prior to this arrest, DMX was recently arrested for speeding over 100 miles per hour on a suspended licence, drugs and animal cruelty. According to a Associated Press article, Maricopa County Sheriff Joe Arpaio said the investigation into DMX committing identity theft started following the investigation into animal neglect at the rapper's home in Phoenix. During the search warrant of DMX's digs -- drugs, guns and 12 malnourished Pit Bulls were found. The remains of three other dogs were found on the property, also.
The type of identity theft DMX allegedly committed is known as medical identity theft. Medical identity theft is a growing phenomenon that causes great harm to it's victims, according to the World Privacy Forum, who performed the first in-depth study of the problem.
Despite the risk it carries, it's probably one of the least studied forms of identity theft. When someone becomes a victim of medical identity theft they not only face having to fix all their financial records, they also face having a lot of erroneous information placed in their medical records.
Medical identity theft victims might receive the wrong treatment, have their insurance used up, and could even be classified as a bad risk when seeking life and medical coverage. They could also fail a medical exam for employment when diseases show up in their medical records that they never had.
While most identity theft victims can correct errors in their credit reports and place alerts or freezes to prevent further fraudulent activity, the victim of medical identity theft doesn't have the same legal rights to clear their files of bad information. In some instances, they aren't even allowed to see what is in their files. Furthermore, medical identity theft victims don't have the right to stop insurers, health care providers and medical clearinghouses from sending this information back and forth to each other.
As medical records become electronic, this poses even greater risks because the information is being transmitted to a variety of databases. Sadly enough, one of the reasons many of these databases are being created is to prevent fraud.
It is also not unheard of for dishonest people in the medical industry to steal identities to submit fraudulent claims to insurance companies and even the government. Authorities within the law enforcement community estimate we are losing $60 billion a year due to Medicare fraud, according to an article in the Washington Post.
If you are interested in learning more about this, or have been a victim of Medical Identity Theft, I recommend reading the Medical Identity Theft Information Page on the World Privacy Forum.
The World Privacy Forum plans to issue a second study on this problem later on this year.

Booking photo of Earl Simmons a.k.a. DMX at the Maricopa County Jail shortly after his arrest.
Sunday, July 13, 2008
IT Policy Compliance Group Issues 2008 Report on Best Practices
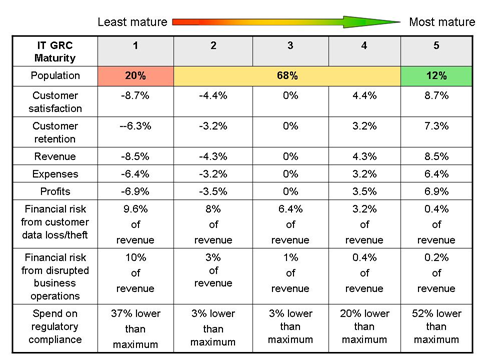
(Courtesy of ITpolicycompliance.com)
The IT Policy Compliance Group just released their annual report on the state of affairs of what they refer to as IT governance, risk and compliance (IT GRC).
The goal of the group is to promote the development of research and information to assist IT and Finance professionals meet their organization's policy and regulatory compliance goals. They do this by providing information for organizations to improve compliance results by providing reports based on primary research.
If you take the time to check out their site, they have other items of interest to anyone charged with the ever growing responsibility of protecting systems from those who have the intent to compromise them.
The recently released report suggests that measuring the value delivered by IT has been traditionally associated with applications that have an impact on customer service, sales, expenses and profit. Unfortunately -- as more organizations have their data compromised -- the result of not protecting information can be a loss of revenue, added expenses (legal costs), and a loss of consumer trust.
This is especially true, if the compromise becomes a matter of public record.
Included in the report are an analysis of recent losses incurred by a large retailer ($530 million) and a large financial services firm ($100 million). The analysis takes into account the loss of revenue due to business disrruption, loss of consumer trust in addition to the harder costs, such as legal expenses. Other analysis includes losses suffered by a automotive manufacturer and a rental and leasing company.
IT departments are constantly being challenged to be up and running 100 percent of the time to maximize efficiency. While doing this, they need to protect their data and adhere to legal and regulatory requirements at the same time.
The challenge is to manage business opportunity and risk at the same time. The 2008 report shows that the firms with the most mature practices in compliance and risk management are doing better and spending less to achieve their goals. This translates into more revenue, profit and customer retention.
The report shows that continuous improvement in risk management and compliance with a focus on operational excellence is paying dividends. Organizations with a mature compliance process have evaluated their processes and made them part of the culture within an organization. While this encompasses the involvement of all facets of an organization, two key items are the support of senior management and training employees to embrace a culture of compliance.
The most mature firms have developed formalized training for their employees, supported by senior management, on subjects like ethics and codes of conduct, IT security and data protection policies, legal compliance, as well as, subjects like sexual harassment and discrimination. They have also developed processes and trained their employees how to deal with emergency situations.
The human factor is always the key to success in any organization. It makes sense that successful organizations focus their efforts through their most valuable resources, which are human beings. Very few exploits are successful without a healthy dose of social engineering.
Also of interest in this informative report is an analysis of results by industry and size. One shoe doesn't necessarily fit all and taking the time to examine all the different types of organizations that use technology to accomplish their goals makes the report a valuable read.
The report, which is located on ITpolicycompliance.com, is only available to members of the site. Saying that, the site is soliciting new members and the sign-up process is simple.
Besides this report, the site has a lot of other valuable information on it, also. I would recommend the site and it's resources to anyone interested in the mysterious world of compliance because it takes it to the level of making sense and developing best practices that will benefit the overall objectives of any organization.
UC Irvine Staff Nails ID Thief in Texas
A former UnitedHealthCare worker, who stole the personal and financial information of at least 1100 University of California, Irvine students has been arrested in Dallas, Texas.
Michael Tyrone Thomas, of Fort Worth, was arrested at his home and is being held on $300,000 bail. The authorities are alleging Thomas stole the information while working at UnitedHealthCare in December 2007. They are also charging that Thomas used the information to fill out fraudulent tax returns using 163 identities stolen in the caper.
According to the Houston Chronicle, a spokesman for UnitedHealthCare didn't return their call concerning the arrest on Friday. I went to the UnitedHealthCare site and found nothing mentioned about this case as of this writing.
It appears that the investigation was initiated by the UC Irvine Police after students started complaining about identity theft in March. Specifically, they complained about someone using their information to fill out bogus tax returns. University computer experts took a look at their systems and found no signs of a breach. Subsequently, University Police investigating the case discovered all the students were enrolled in a insurance program administered by UnitedHealthCare.
A press release on the UC Irvine site gave credit to UCI Police Sergeants Tony Frisbee, Shaun Devlin and Corporal Caroline Altamirano for working closely on the case with the Dallas District Attorney's Office. The release indicates that they expect additional arrests and that the IRS will be investigating the tax fraud implications in the case.
Recently, the National Taxpayer Advocate, issued a report to Congress indicating that tax fraud involving the use of stolen identities has grown 644 percent in the past four years. In a lot of these cases, forged W-2's are used to claim an earned income credit, which can net the fraudster thousands of dollars per return.
In my post on this story, I mentioned that the IRS has a dedicated page to assist identity theft victims when their information has been used to commit tax fraud. The Houston Chronicle article mentioned that UnitedHealthCare will be offering free credit monitoring and that UCI will be offering loans to the affected students. It also mentioned that UCI Police Chief, Paul Henisey doesn't think the rest of the names were used because the reports of identity theft dropped off in late June.
Free credit monitoring seems to be the standard offer to victims when a data breach is disclosed, but it doesn't necessarily reveal all forms of identity theft. Credit bureaus do not track what information is being used to file a tax return and would be worthless in the already known cases. Other examples when credit monitoring might not be the end-all solution to identity theft protection are medical benefit fraud, employment fraud, government benefit fraud, some forms of check fraud and last, but not least, when it is used to commit crimes of other than a financial nature.
If I were one of the affected UC Irvine students, I wouldn't turn down the free credit monitoring (it does help in a lot of instances), but I would also visit the Identity Theft Resource Center's Financial Identity Theft - More Complex Cases page to educate myself a little further.
So far as Chief Henisey's prediction that this case is over -- I certainly hope it is -- but it wouldn't be prudent for everyone to let their guard down just yet. Information is bought and sold in a lot of places (including over the Internet) for the purpose of identity theft. There is no way of telling, whether or not, any of this information was passed to someone else for a profit.
Saying that, it's refreshing to see the culprit caught in this case and the UC Irvine Police Department (along with other University staff) did an excellent job in their investigation. It isn't very often when one of these cases is traced to the person behind it.
DOD Analyst Convicted for Selling Information to China
On Friday, the Department of Justice announced that one Gregg William Bergersen of Alexandria, Virginia was sentenced to 57 months in prison (plus three years of supervised release) for disclosing secret information to a naturalized American citizen of Chinese descent (Tai Shen Kuo), who was then providing it to the People's Republic of China.
In his day job, Gregg Bergersen was a Department of Defense Analyst.
Kuo provided Bergersen with gifts, cash payments, dinners and gambling money in exchange for the information. The information involving military sales to Taiwan was then passed to Kuo's handler, an official of the People's Republic of China.
The official DOJ press release states that Bergersen didn't know the information was going to China. It would be interesting to discover, who he thought it was going to?
Kuo, who was found guilty on May 13th, is currently awaiting sentencing on August 8th and faces life in prison.
On May 28th, Yu Xin Kang, also of New Orleans pleaded guilty to aiding and abetting an unregistered agent of the People's Republic of China. According to court documents, Kang sometimes assisted Kuo in providing the stolen information to the unnamed foreign official. Kang faces ten years in prison.
Last year, another naturalized American citizen of Chinese descent, Chi Mak, was convicted of selling sensitive defense technology to China. This case was a family affair and Mak's sister in law and brother were caught by the FBI trying to board a plane to China with three encrypted CD's containing the stolen information.
The FBI site covered the Bergersen/Kuo case and another one involving a Boeing engineer, Dongfan “Greg” Chung, in a recent press release. Allegedly Chung was tied into the Mak case and sold information on the Space Shuttle and military aircraft to the People's Republic of China.
Although, the government isn't commenting much there is speculation that they are investigating information being stolen from Commerce Secretary Carlos M. Gutierrez's laptop during a recent visit to China. It is alleged that this information was used to hack into government computers.
Hacking incidents traced to the Chinese, although always denied by the PRC, have been reported all over North America, Europe and even Asia. A good place to learn about Chinese hacking activity is a site (maintained by a former DOD official) called The Dark Visitor (Information on Chinese Hacking) .
The Chinese are also suspected (in a lot of instances) of stealing corporate information. According to sources within the technology industry, it isn't recommended to carry laptops or other personal data storage devices when travelling in China.
On a personal note, I believe a lot of this is enabled by our free trade agreement with the People's Republic of China. While this agreement is lucrative for a few corporate entities -- the wholesale theft of intellectual property, counterfeiting, unsafe and defective products, as well as, all the human rights violations in China call for taking a hard and educated look at what is going on.
The problem is will special interests -- who represent the corporate entities making a lot of money from this -- prevent our leadership in Washington from taking effective action against what is becoming an alarming issue?
If you suspect anyone of selling government secrets, you can report them to the FBI by submitting an anonymous tip online.
Wednesday, July 09, 2008
Stolen Identities Used to File Tax Returns Grows 644 percent
Nina Olson, the National Taxpayer Advocate, warned Congress in a report that identity theft is becoming one of the biggest issues facing taxpayers today. The two main reasons cited were identities stolen to file fraudulent refunds and to obtain employment.
As more pressure is being placed on employers to ensure their employees have a social security number that matches a name, more illegal immigrants are using an identity that matches the social security number on their employment records. No-match legislation, which was introduced by the Department of Homeland Security has been held up in a Federal Court, but some States are taking matters into their own hands. I also read an interesting article in the Twin Cities Daily Planet indicating that these letters are already causing action to be taken at some employers.
Prior to no-match legislation, anyone could simply make up a social security number and it would pass muster for employment reasons.
No matter what side of the fence someone is on from a political perspective, these no-match letters are likely to increase the amount of identity theft we are seeing in regards to tax returns. With all the stolen personal information and counterfeit documents being sold by organized criminals -- it probably isn't going to be hard to use someone else's identities for employment reasons. Stolen identities are available in a lot of places (including the Internet) and counterfeit documents are hawked on street corners across the country.
Another thing I've written about is the increasing amount of fraud being seen using the earned income credit to get a quick refund using someone else's information. The Earned Income Credit -- which is designed as a windfall of several thousand dollars for lower income people -- is easily manipulated by individuals and on a larger scale, by dishonest tax preparers to scam the IRS.
Last year, a large Jackson Hewitt franchisee was charged by the Justice Department for (allegedly) encouraging this type of fraud. Dishonest tax preparers often recruit low income people to used a forged W-2 (forms are easily available in Office Supply Stores) and get a quick refund of thousands of dollars. In other cases, this is also done using stolen identities, causing the legitimate person a lot of heartache when they go to file their return. Ironically, in years past, there have even been reports of this type of fraud being committed by prisoners who weren't being monitored, very well!
Easily available W-2 blanks and the seeming inability of the IRS to verify payroll information are two of the enabling factors of this type of fraud.
The recent report indicates that the IRS will start using a computer program to identify potential identity theft cases next year. It is also considering establishing an office to assist identity theft victims.
Olsen also plans to monitor the use of private debt collectors by the IRS, carefully. The reasons cited are a lack of transparency on the procedures used by these agencies and the potential for people's rights to be violated by these agencies.
Stories of identity theft victims being harassed by collections agencies for debts they were not responsible for are well documented and have caused innocent people a lot of pain and suffering.
Another thing to consider is that since this type of identity theft normally doesn't show up on a credit bureaus very quickly, we probably have a lot of people purchasing identity theft protection that will not necessarily detect the fact that they have become a victim. The Identity Theft Resource Center has information on how to check if your social security number is being used and what to do about it. The IRS also has a page on their site on how to deal with this issue.
The IRS also offers more information on their site about the Taxpayer Advocate Service and how they can assist the average person.
All in all, I consider this report timely and an issue that needs to be taken seriously given an already exploding statistic and the potential for this phenomenon to grow.
Friday, July 04, 2008
California Lottery Nails Dishonest Retailers
When you cash in a small lottery prize at a lottery retailer, the amount might not exactly what you were were entitled to receive.
On 7/1/08, the California Lottery announced that they are using undercover agents to sting dishonest retailers, who cheat lottery winners out of their prizes. The press release on this matter pointed to a case in Morgan Hill, California where a dishonest retailer (and another individual) are being charged with grand theft of lottery tickets ranging in value from $500 to $25,000.
I decided to see if I could find any additional information on arrests and discovered another one that was reported by cbs13.com in Lodi, California. CBS 13 in Sacramento, with cameras rolling, approached Baljut Kang (one of the two arrested in Lodi), who refused to talk at first. Eventually, Kang stated to the reporter that the undercover agents found "some ticket in the garbage," which made them think she and her son were committing fraud (?).
According to the article, an undercover agent turned in one ticket worth $990 receiving only $24. Another ticket was presented at the retailer worth $25,000 and the agent was paid $10 for it. The article also states that this was the result of a statewide lottery sting. Other retailers were caught in Southern California.
The official press release indicates that this is the first enforcement effort of this kind anywhere in the country. This made me wonder if other States should run sting operations, also?
While dishonest retailers getting caught cheating customers is something new, lottery scams are big business for criminals. Spam e-mails, unsolicited telephone calls and even snail mails are used to dupe people into thinking they have won the lottery. Frequently, a person is then asked to negotiate a fraudulent instrument to cover tariffs and taxes and wire the money across an International border.
The California lottery has an interesting page, which can be seen on their website warning the public about this type of activity. In February, I did a post on the eve of a $270 Mega Million Lottery prize, about fraudsters attempting to impersonate the California lottery to trick unsuspecting people into cashing worthless checks.
Please note that scams -- where unsuspecting people are duped into cashing worthless checks and wiring the money before the financial institution catches on -- aren't limited to the lottery variety. Other varieties involving bogus financial instruments include work-at-home (job) scams, secret shopper, romance and auction scams. Known bogus items in circulation are Postal Money Orders, Travelers Express (MoneyGram) Money Orders, American Express Gift Cheques and Visa Travelers Cheques. A good site to learn more about scams involving fake checks is FakeChecks.org.
In California when you claim a ticket for a prize under $600, the retailer has to validate it in a machine, which prints a receipt showing exactly how much the prize was for. A good idea is to make sure you take a look at this receipt to ensure you are getting the right amount of money.
If you note suspicious activity, I'm sure that the dedicated law enforcement personnel at the California Lottery would like to hear from you. They can be reached at 1-800-LOTTERY.
Tuesday, July 01, 2008
Data Theft Grows 68 Percent in 2008
The current study acknowledges that some breaches are under reported and multiple breaches are sometimes reported as a single event. The breach at BNY Mellon and SunGard data were cited as an example of a single event affecting multiple businesses.
The report shows an increase in data breaches at businesses, financial institutions and health/medical institutions. Interestingly enough, breaches that involved the government/military and educational institutions showed a decrease.
Breaches are becoming more technology based, also. Electronic data breaches accounted for 80.7 percent of the total versus 19.3 percent, which were considered paper breaches.
I suspect that the increased activity at businesses and financial institutions is because the goal is to steal financial instruments that already have a cash value associated with them. As the general public has become more aware of the issues surrounding identity theft, opening fraudulent accounts with other people's information is becoming more difficult. More people are reviewing their credit and placing alerts/freezes on their individual reports, either by doing it themselves or paying a service to do it for them. When accounts are stolen that already have disposable spending power or (cash) on them, identity theft protection is unlikely to stop them from being compromised.
Because of the increased awareness, more fraudsters take over accounts instead of trying to open new ones. Most of the current identity theft protection methods being used will not stop this from happening.
So far as the statistic that electronic theft is becoming more prevalent than paper theft, perhaps shredding documents is making stealing paper harder? Of course, it might also mean that the methods to steal information electronically have become more advanced, also. Crimeware kits of the DIY (do-it-yourself) variety have spread this ability to people, who lack the technical skills to do it by themselves. There is a lot of evidence that these kits aren't too hard to purchase over the Internet and that sometimes they even come with technical support.
ID Analytics partnered with the study and added statistical information showing that 39 percent of data exposures were caused by missing or stolen devices in 2007. Their statistics also show that malicious intent in data breaches is a growing trend. Malicious intent categories include insider theft and access into account information by external methods (hacking).
A new trend, not specifically mentioned in the report, is large caches of stolen information being discovered that no one knew about before. Yesterday, Dark Reading announced that SecureWorks found one of these caches. Finjan has recently reported finding pretty much the same thing located on what they refer to as "crimeservers" on the Internet. The announcement by SecureWorks reported that hackers are using a trojan, called "Coreflood" also known as "AFCore."
SecureWorks reported that this trojan has gone undetected for a number of years and has compromised corporations, government agencies, healthcare agencies and "others." In this attack, one work station would be compromised and the hacker would wait for an administrator to log on. Once the administrator logged on to the infected work station, the hacker would then use the administrator's privileges to infect entire systems. This "hack" is being used to grab user names, passwords and even entire pages of information. Please note (my speculation) that this type of exploit is probably being used to steal more than financial information, also.
Given the fact that SecureWorks mentions government sites being hacked in this manner, there is no telling what the intent might be or who the information is being sold to (my speculation).
To the best of my knowledge, neither SecureWorks or Finjan have disclosed exactly who has been compromised or the exact details of the information to the general public.
This should lead the average person to believe that the problem of data breaches is far greater than anyone knows. The ITRC study explains why this is a problem when compiling any study on this subject.
Besides the ITRC, there are a lot of dedicated people gathering statistical information on data breaches. While they can only track information on the known occurrences, these people do a lot to educate the rest of us and raise the awareness level of what is becoming a growing problem.
The report gives credit to PogoWasRight, Attrition.org, breachblog.com, the Maryland and New Hampshire Attorney General breach notification lists and other sources that were used to compile this report.
The ITRC is a non profit organization designed to help businesses and people protect themselves from this clear and present danger to all of us. If you are interested in this problem, their site is a good place to educate yourself.
