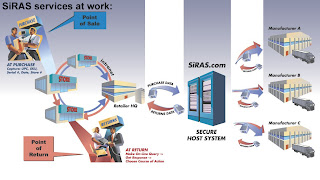
Graphic demonstration of anti-theft technology courtesy of SIRAS.com.
Criminals, who steal goods, whether with bogus financial instruments, or by more physical means might be in for a little surprise if the merchandise is protected by SIRAS PI.
Last week, SIRAS made this announcement in a press release:
SIRAS.com, the pioneer in Point-Of-Sale Electronic Product Registration used by leading manufacturers and retailers, has announced the nationwide launch of SIRAS P.I., a groundbreaking initiative to aid law enforcement officials in determining whether products they recover are, in fact, stolen, and if so, from where. Piloted by the Mesa, Arizona Police Department, SIRAS’s P.I. (Product Information) Database has already proven to be effective in helping law enforcement officials identify stolen items, report suspicious items, and apprehend and convict thieves. The database will be available, free of charge, to police and law enforcement agencies nationwide.
The way SIRAS works is simple, but effective. It tracks a product by recording the UPC (Universal Product Code) and the product serial number. SIRAS has the capability to determine where merchandise was stolen, whether from a merchant, manufacturer, or individual.
Earlier this year, SIRAS did some testing that revealed a substantial reduction in TV and MP3 player losses on products, where their technology was being used.
If deployed properly at the merchant level -- it could also determine how an item was purchased, and whether or not -- the method of payment used was legitimate. In theory, a merchant could also use the technology to impact credit card chargeback and fraud check losses.
I say "deployed properly" and "in theory" because the information to accomplish this (sales data) belongs to the company using SIRAS technology. Because of this, the capability to track sales information would have to be implemented inside the company. At most larger companies, this information is already tracked and analyzed to prevent and detect dishonest activity.
For years, most high-theft (shrink) merchandise has been secured so a thief can't merely pick it up from a shelf. When high-theft merchandise that was secured is stolen, it's normally because of one of two reasons. It was purchased with a bogus financial instrument, or an insider was involved in the theft.
Other reasons for secured merchandise being stolen might be a theft, directly from the manufacturer, or a theft during the shipping (transport) process. In these instances, if the merchandise was registered at the manufacturer, SIRAS can identify the point of compromise, also.
Technology has made it a lot easier for criminals to obtain and use fraudulent forms of payment. Information being compromised (data breaches) and anonymous places to communicate like Internet chat rooms, have given a lot of common criminals access to bogus financial instruments.
Along with the increased availability of fraudulent forms of payment, obtaining counterfeit identification documents has become fairly easy, and the identity used on them normally belongs to someone else. This has made it easy for a lot of retail criminals to operate as someone else.
Because of these new trends, current systems that record personal information to prevent fraud are becoming less effective than they use to be. I often wonder (no one probably really knows) how much of the information contained in them is incorrect.
In the recent data breach at TJX, one of the systems compromised was their refund database. Stories have circulated recently about the wrong people being pegged as frequent refunders, or bad check writers after their identities were stolen.
Neither one of these situations fosters good will, or trust with customers. Besides that, data breaches are becoming costly. The last I heard TJX has spent approximately $256 million dealing with the breach. With pending litigation, the cost is liable to keep going up.
With SIRAS, using personal information isn't necessary to determine, whether or not, a return is legitimate. SIRAS already has proven to be highly effective in reducing refund fraud without asking for one item of personal information.
An example of how some of the TJX data was used in a retail theft scenario can be seen, here.
Given that criminals that steal merchandise want to turn it into money, two methods are normally used. They either refund it somewhere, or fence it. Auction sites provide an easy and when combined with account-takeover activity (anonymous) venue for criminals to fence merchandise.
In the auction world, seller accounts are taken over all the time. This normally occurs when seller accounts are compromised by a phenomenon known as phishing. Phishing occurs when a person is tricked into giving up their access information after receiving a spam e-mail.
Compromised seller accounts are sold on the Internet the same way financial information is, and there is a trend in DIY (do-it-yourself) phishing kits being sold that enable non-technical criminals to get into the game.
eBay and PayPal are two of the most heavily phished brands. Once these accounts are compromised (taken over), they are used by criminals to fence merchandise and launder the monetary proceeds of their illicit sales.
Another growing trend related to phishing is when malware, also sometimes known as crimeware is used to steal information. The difference here is information is stolen from systems automatically (normally by keylogging software) and social engineering (trickery) is no longer necessary to get people to give up information.
Malware is often picked up by a computer system by clicking on a spam e-mail link, or by visiting a website designed to inject the software on a system. PC World recently did one of the many stories floating around about malware being sold on the Internet in the form of DIY kits.
In the story they wrote:
The global market for criminal malware now operates like a supermarket, complete with special offers and volume discounts, a security company has discovered.
Here again, this capability enables not very technically inclined criminals to get into the game. This has become a growing problem and I expect it to get worse before it gets better.
With the availability of all this personal and financial information, being sold on an economy of scale, current fraud protection systems are routinely being compromised by a lot of criminals.
There is an old saying in the investigations world, which is if you want to solve a crime, the easiest way is to follow the money.
SIRAS takes this one step further by tracking both the merchandise and can track the money ( if programmed to do so by the user). When you do this, the odds are far greater that the true culprit will be identified. They are normally associated with either the money, and or the merchandise.
Since the technology records both physical and UPC information, the database can determine exactly where the merchandise was compromised (stolen). Given that many merchants use digital video systems -- which are capable of storing video footage for a long time, it's also possible to obtain video evidence of the original transaction -- when sales information has been programmed to tie into the technology.
SIRAS has been used by select manufacturers and merchants for several years now -- however a new initiative, SIRAS PI, which was tested with Mesa PD -- makes the database available to law enforcement agencies free of charge.
Law enforcement can access the database either via the Internet, or by telephone. They can also add items to the database when they are reported stolen. If someone later tries to refund the merchandise at a participating retailer, the transaction can be automatically flagged.
Although a lot of fencing now occurs on the Internet, the technology is equally as effective in investigating more traditional property crimes, also. The bottom line is once merchandise is discovered, it can be tracked by SIRAS, if the item has been registered.
Recently, Chris Hansen (MSNBC), did a story about iPod theft. When Apple was approached about tracking the merchandise using Apple's registration database, they decided not to cooperate with MSNBC.
Undaunted by this, MSNBC purchased a bunch of iPods and engineered the registration disc to send them the information when the iPod was registered. They then left the iPods (new in the box) unattended, let them get stolen and tracked them to the crooks once the iPod was registered.
Chris Hansen made an excellent point on how databases can track stolen merchandise -- but in this instance, brand new iPods had to be left in public places to be stolen -- then registered to make the point.
If Apple used SIRAS technology to protect their merchandise -- it would have already been traceable, even if it was stolen from an individual -- who didn't provide the thief with the registration disc. It also would eliminate privacy concerns, which might be why Apple didn't want to cooperate with the MSNBC investigation?
When registering any product, a lot of personal information is normally asked for.
In any event, most criminals of the smarter variety aren't going to provide their personal information in the registration process. Most of them shy away from doing things, which might get them caught.
It would be interesting to have MSNBC, or another investigative news source do the same story with merchandise protected by SIRAS. The story might expose more than people, who stole because of an almost "too good to be true" opportunity was provided to them.
MSNBC iJacking story, here.
This brings up another potential benefit to this technology. Expensive portable electronics and other expensive toys like mountain bikes are stolen from the people who buy them (customers) all the time. Using SIRAS technology might even be a selling point that instills customer trust in the product they are purchasing.
This technology has prevention/investigation applications for corporations, law enforcement agencies and individuals, alike. It also doesn't require using people's personal information, which isn't as effective as it used to be, and is becoming more unpopular all the time.
In my opinion, this technology has the ability to make it a lot harder to get away with stealing merchandise and converting it into money.
Of course, the more it is used, the more effective it will become. Databases have a tendency to do this, or become more useful as they contain more information.
There are a lot of anti-theft/fraud technologies that claim to prevent theft/fraud. Very few of them also claim to be able to go after and hold the criminals committing the fraud/theft personally accountable.
The last I heard, most criminals still fear getting caught!
If you would like more information on the organized trade in counterfeit identification documents, the story of Suad Leija can be seen, here.
Suad's story has been covered extensively in the media, including by Lou Dobbs. Currently, she is writing a book and I keep in touch with her occasionally.
More information about bogus financial instruments can be seen, here and here.
A chronology of data breaches is compiled by the Privacy Rights Clearinghouse, here.
The best source on phishing is the Anti-Phishing Working Group and if you are interested in learning even more about phishing and want to see some totally fake banking sites, Artists Against 419 is another good place to visit.
Last, but not least, if you are interested in learning more about SIRAS PI, you can do so by visiting their site, here.


